mirror of
https://github.com/qodo-ai/pr-agent.git
synced 2025-07-21 04:50:39 +08:00
Compare commits
2 Commits
hl/fix_azu
...
es/api_key
| Author | SHA1 | Date | |
|---|---|---|---|
| 72ad76692b | |||
| 5dfd696c2b |
@ -9,9 +9,8 @@ This integration enriches the review process by automatically surfacing relevant
|
||||
|
||||
**Ticket systems supported**:
|
||||
|
||||
- [GitHub](https://qodo-merge-docs.qodo.ai/core-abilities/fetching_ticket_context/#github-issues-integration)
|
||||
- [Jira (💎)](https://qodo-merge-docs.qodo.ai/core-abilities/fetching_ticket_context/#jira-integration)
|
||||
- [Linear (💎)](https://qodo-merge-docs.qodo.ai/core-abilities/fetching_ticket_context/#linear-integration)
|
||||
- GitHub
|
||||
- Jira (💎)
|
||||
|
||||
**Ticket data fetched:**
|
||||
|
||||
@ -76,17 +75,13 @@ The recommended way to authenticate with Jira Cloud is to install the Qodo Merge
|
||||
|
||||
Installation steps:
|
||||
|
||||
1. Go to the [Qodo Merge integrations page](https://app.qodo.ai/qodo-merge/integrations)
|
||||
|
||||
2. Click on the Connect **Jira Cloud** button to connect the Jira Cloud app
|
||||
|
||||
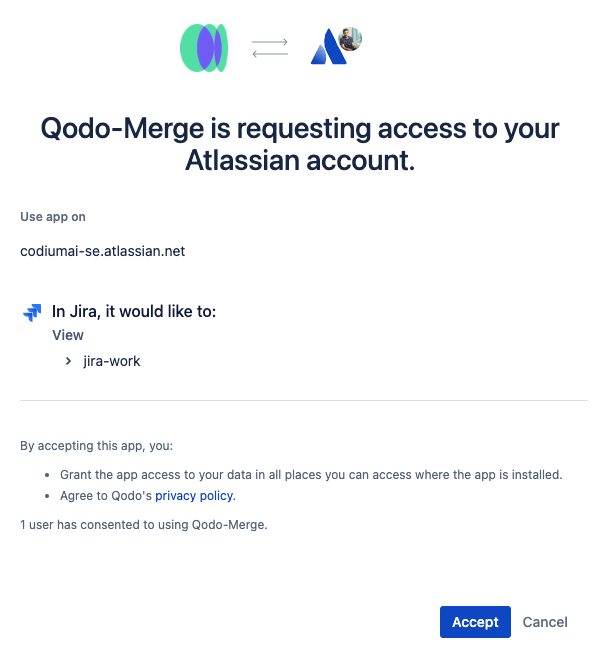
3. Click the `accept` button.<br>
|
||||
1. Click [here](https://auth.atlassian.com/authorize?audience=api.atlassian.com&client_id=8krKmA4gMD8mM8z24aRCgPCSepZNP1xf&scope=read%3Ajira-work%20offline_access&redirect_uri=https%3A%2F%2Fregister.jira.pr-agent.codium.ai&state=qodomerge&response_type=code&prompt=consent) to install the Qodo Merge app in your Jira Cloud instance, click the `accept` button.<br>
|
||||
{width=384}
|
||||
|
||||
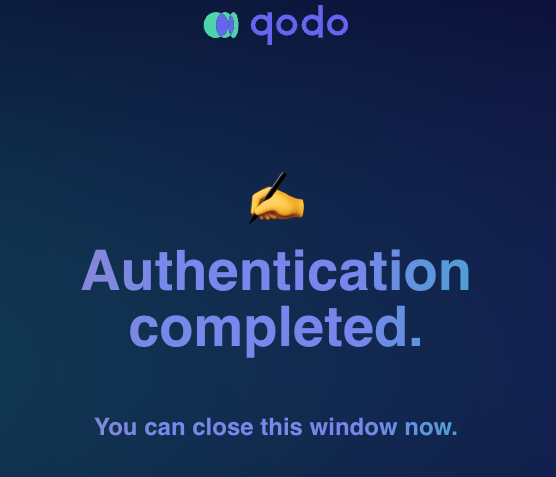
4. After installing the app, you will be redirected to the Qodo Merge registration page. and you will see a success message.<br>
|
||||
2. After installing the app, you will be redirected to the Qodo Merge registration page. and you will see a success message.<br>
|
||||
{width=384}
|
||||
|
||||
5. Now Qodo Merge will be able to fetch Jira ticket context for your PRs.
|
||||
3. Now Qodo Merge will be able to fetch Jira ticket context for your PRs.
|
||||
|
||||
**2) Email/Token Authentication**
|
||||
|
||||
@ -305,45 +300,3 @@ Name your branch with the ticket ID as a prefix (e.g., `ISSUE-123-feature-descri
|
||||
[jira]
|
||||
jira_base_url = "https://<JIRA_ORG>.atlassian.net"
|
||||
```
|
||||
|
||||
## Linear Integration 💎
|
||||
|
||||
### Linear App Authentication
|
||||
|
||||
The recommended way to authenticate with Linear is to connect the Linear app through the Qodo Merge portal.
|
||||
|
||||
Installation steps:
|
||||
|
||||
1. Go to the [Qodo Merge integrations page](https://app.qodo.ai/qodo-merge/integrations)
|
||||
|
||||
2. Navigate to the **Integrations** tab
|
||||
|
||||
3. Click on the **Linear** button to connect the Linear app
|
||||
|
||||
4. Follow the authentication flow to authorize Qodo Merge to access your Linear workspace
|
||||
|
||||
5. Once connected, Qodo Merge will be able to fetch Linear ticket context for your PRs
|
||||
|
||||
### How to link a PR to a Linear ticket
|
||||
|
||||
Qodo Merge will automatically detect Linear tickets using either of these methods:
|
||||
|
||||
**Method 1: Description Reference:**
|
||||
|
||||
Include a ticket reference in your PR description using either:
|
||||
- The complete Linear ticket URL: `https://linear.app/[ORG_ID]/issue/[TICKET_ID]`
|
||||
- The shortened ticket ID: `[TICKET_ID]` (e.g., `ABC-123`) - requires linear_base_url configuration (see below).
|
||||
|
||||
**Method 2: Branch Name Detection:**
|
||||
|
||||
Name your branch with the ticket ID as a prefix (e.g., `ABC-123-feature-description` or `feature/ABC-123/feature-description`).
|
||||
|
||||
!!! note "Linear Base URL"
|
||||
For shortened ticket IDs or branch detection (method 2), you must configure the Linear base URL in your configuration file under the [linear] section:
|
||||
|
||||
```toml
|
||||
[linear]
|
||||
linear_base_url = "https://linear.app/[ORG_ID]"
|
||||
```
|
||||
|
||||
Replace `[ORG_ID]` with your Linear organization identifier.
|
||||
@ -12,11 +12,10 @@ It also outlines our development roadmap for the upcoming three months. Please n
|
||||
- **Scan Repo Discussions Tool**: A new tool that analyzes past code discussions to generate a `best_practices.md` file, distilling key insights and recommendations. ([Learn more](https://qodo-merge-docs.qodo.ai/tools/scan_repo_discussions/))
|
||||
- **Enhanced Models**: Qodo Merge now defaults to a combination of top models (Claude Sonnet 3.7 and Gemini 2.5 Pro) and incorporates dedicated code validation logic for improved results. ([Details 1](https://qodo-merge-docs.qodo.ai/usage-guide/qodo_merge_models/), [Details 2](https://qodo-merge-docs.qodo.ai/core-abilities/code_validation/))
|
||||
- **Chrome Extension Update**: Qodo Merge Chrome extension now supports single-tenant users. ([Learn more](https://qodo-merge-docs.qodo.ai/chrome-extension/options/#configuration-options/))
|
||||
- **Installation Metrics**: Upon installation, Qodo Merge analyzes past PRs for key metrics (e.g., time to merge, time to first reviewer feedback), enabling pre/post-installation comparison to calculate ROI.
|
||||
|
||||
|
||||
=== "Future Roadmap"
|
||||
- **Smart Update**: Upon PR updates, Qodo Merge will offer tailored code suggestions, addressing both the entire PR and the specific incremental changes since the last feedback.
|
||||
- **CLI Endpoint**: A new Qodo Merge endpoint will accept lists of before/after code changes, execute Qodo Merge commands, and return the results.
|
||||
- **Simplified Free Tier**: We plan to transition from a two-week free trial to a free tier offering a limited number of suggestions per month per organization.
|
||||
- **Best Practices Hierarchy**: Introducing support for structured best practices, such as for folders in monorepos or a unified best practice file for a group of repositories.
|
||||
- **Installation Metrics**: Upon installation, Qodo Merge will analyze past PRs for key metrics (e.g., time to merge, time to first reviewer feedback), enabling pre/post-installation comparison to calculate ROI.
|
||||
@ -144,26 +144,16 @@ extra_instructions = "..."
|
||||
Meaning the `review` tool will run automatically on every PR, without any additional configurations.
|
||||
Edit this field to enable/disable the tool, or to change the configurations used.
|
||||
|
||||
### Auto-generated PR labels by the Review Tool
|
||||
### Auto-generated PR labels from the Review Tool
|
||||
|
||||
!!! tip ""
|
||||
|
||||
The `review` can tool automatically add labels to your Pull Requests:
|
||||
The `review` tool automatically adds two specific labels to your Pull Requests:
|
||||
|
||||
- **`possible security issue`**: This label is applied if the tool detects a potential [security vulnerability](https://github.com/qodo-ai/pr-agent/blob/main/pr_agent/settings/pr_reviewer_prompts.toml#L103) in the PR's code. This feedback is controlled by the 'enable_review_labels_security' flag (default is true).
|
||||
- **`review effort [x/5]`**: This label estimates the [effort](https://github.com/qodo-ai/pr-agent/blob/main/pr_agent/settings/pr_reviewer_prompts.toml#L90) required to review the PR on a relative scale of 1 to 5, where 'x' represents the assessed effort. This feedback is controlled by the 'enable_review_labels_effort' flag (default is true).
|
||||
- **`ticket compliance`**: Adds a label indicating code compliance level ("Fully compliant" | "PR Code Verified" | "Partially compliant" | "Not compliant") to any GitHub/Jira/Linea ticket linked in the PR. Controlled by the 'require_ticket_labels' flag (default: false). If 'require_no_ticket_labels' is also enabled, PRs without ticket links will receive a "No ticket found" label.
|
||||
- **`possible security issue`**: This label is applied if the tool detects a potential [security vulnerability](https://github.com/qodo-ai/pr-agent/blob/main/pr_agent/settings/pr_reviewer_prompts.toml#L103) in the PR's code. This feedback is controlled by the 'enable_review_labels_security' flag.
|
||||
- **`review effort [x/5]`**: This label estimates the [effort](https://github.com/qodo-ai/pr-agent/blob/main/pr_agent/settings/pr_reviewer_prompts.toml#L90) required to review the PR on a relative scale of 1 to 5, where 'x' represents the assessed effort. This feedback is controlled by the 'enable_review_labels_effort' flag.
|
||||
|
||||
|
||||
### Blocking PRs from merging based on the generated labels
|
||||
|
||||
!!! tip ""
|
||||
|
||||
You can configure a CI/CD Action to prevent merging PRs with specific labels. For example, implement a dedicated [GitHub Action](https://medium.com/sequra-tech/quick-tip-block-pull-request-merge-using-labels-6cc326936221).
|
||||
|
||||
This approach helps ensure PRs with potential security issues or ticket compliance problems will not be merged without further review.
|
||||
|
||||
Since AI may make mistakes or lack complete context, use this feature judiciously. For flexibility, users with appropriate permissions can remove generated labels when necessary. When a label is removed, this action will be automatically documented in the PR discussion, clearly indicating it was a deliberate override by an authorized user to allow the merge.
|
||||
Note: The `possible security issue` label highlights potential security risks. You can configure a GitHub Action to [prevent merging](https://medium.com/sequra-tech/quick-tip-block-pull-request-merge-using-labels-6cc326936221) PRs that have this label.
|
||||
|
||||
### Extra instructions
|
||||
|
||||
|
||||
@ -350,8 +350,7 @@ class AzureDevopsProvider(GitProvider):
|
||||
get_logger().debug(f"Skipping publish_comment for temporary comment: {pr_comment}")
|
||||
return None
|
||||
comment = Comment(content=pr_comment)
|
||||
# Set status to 'active' to prevent auto-resolve (see CommentThreadStatus docs)
|
||||
thread = CommentThread(comments=[comment], thread_context=thread_context, status='active')
|
||||
thread = CommentThread(comments=[comment], thread_context=thread_context, status="closed")
|
||||
thread_response = self.azure_devops_client.create_thread(
|
||||
comment_thread=thread,
|
||||
project=self.workspace_slug,
|
||||
|
||||
60
pr_agent/scripts/qm_endpoint_auth/gen_api_key.py
Normal file
60
pr_agent/scripts/qm_endpoint_auth/gen_api_key.py
Normal file
@ -0,0 +1,60 @@
|
||||
import requests
|
||||
import json
|
||||
import webbrowser
|
||||
|
||||
BASE_URL="https://api.cli.qodo.ai"
|
||||
QM_CMD_ENDPOINT_KEY_NAME="qm_cmd_endpoint"
|
||||
|
||||
def get_api_key():
|
||||
try:
|
||||
url = f"{BASE_URL}/v1/auth/cli-auth?key_name={QM_CMD_ENDPOINT_KEY_NAME}"
|
||||
# Make HTTP request
|
||||
response = requests.get(url, stream=True, # For SSE (Server-Sent Events)
|
||||
headers={'Accept': 'text/event-stream'})
|
||||
|
||||
# Parse Server-Sent Events format
|
||||
# Look for line:
|
||||
# data: {"auth_url":"https:\/\/auth.qodo.ai\/?extensionId=Codium.codium&extensionQuery=<SOME UUID>&uriScheme=cli"}
|
||||
opened_auth_url = False
|
||||
for line in response.iter_lines(decode_unicode=True):
|
||||
if line and line.startswith('data:'):
|
||||
data_json = line.replace('data: ', '', 1)
|
||||
try:
|
||||
data = json.loads(data_json)
|
||||
if not opened_auth_url:
|
||||
if 'auth_url' not in data:
|
||||
print(f"Expected an auth_url, but couldn't find one.")
|
||||
return None
|
||||
print(f"Got url: {data['auth_url']}.")
|
||||
# Unescape the URL
|
||||
auth_url = data['auth_url'].replace('\\/', '/')
|
||||
webbrowser.open(auth_url)
|
||||
opened_auth_url = True
|
||||
else:
|
||||
api_key = data.get('api_key', None)
|
||||
print(f"Got api key: {api_key}.")
|
||||
if not api_key:
|
||||
print(f"Expected an api_key, but couldn't find one.")
|
||||
return api_key
|
||||
except json.JSONDecodeError as e:
|
||||
print(f"Error parsing JSON: {e}")
|
||||
return None
|
||||
|
||||
print("No data line found in response")
|
||||
return None
|
||||
|
||||
except requests.exceptions.RequestException as e:
|
||||
print(f"Error making HTTP request: {e}")
|
||||
return None
|
||||
|
||||
def run():
|
||||
"""This is the function serving as this file's entry point, as defined in pyproject.toml"""
|
||||
print("Attempting to generate an API Key...")
|
||||
|
||||
api_key = get_api_key()
|
||||
if api_key:
|
||||
print(f"Please use the following API Key: {api_key} when invoking QM endpoint.")
|
||||
print(f"For example: curl -i --header \"Authorization: ApiKey {api_key}\" -X POST https://<QM ENDPOINT SERVER ADDR>/api/v1/qodo_merge_cmd")
|
||||
|
||||
if __name__ == "__main__":
|
||||
run()
|
||||
4
pr_agent/scripts/qm_endpoint_auth/gen_api_key.sh
Normal file
4
pr_agent/scripts/qm_endpoint_auth/gen_api_key.sh
Normal file
@ -0,0 +1,4 @@
|
||||
curl -s --no-buffer "https://api.cli.qodo.ai/v1/auth/cli-auth" | while read line; do
|
||||
[[ $line == data:*auth_url* ]] && open "$(echo "$line" | sed 's/.*"auth_url":"\([^"]*\)".*/\1/' | sed 's/\\//g')"
|
||||
[[ $line == data:*api_key* ]] && echo "✅ Authentication successful! API key saved.\n📋 Your API key: $(echo "$line" | sed 's/.*"api_key":"\([^"]*\)".*/\1/')" && break
|
||||
done
|
||||
@ -44,6 +44,7 @@ include = [
|
||||
|
||||
[project.scripts]
|
||||
pr-agent = "pr_agent.cli:run"
|
||||
gen-api-key = "pr_agent.scripts.qm_endpoint_auth.gen_api_key:run"
|
||||
|
||||
[tool.ruff]
|
||||
line-length = 120
|
||||
|
||||
Reference in New Issue
Block a user